SSL VPN with Fortigate firewalls - Part II (Certificate authentication)
In last blog we have looked at how to configure SSL VPN in fortigate firewall with username/password authentication. Now we will replicate the same setup but with certificate authentication. Our setup will use user-certificate; not machine-certificate authentication.
Our topology looks like below -
The topology is very simple as our goal is to look at the SSL VPN implementation in Fortigate firewalls. The firewall has one internal network (10.10.1.0/24) where we have one windows server (Srv-Win-Ad-01 - 10.10.1.25/24) which is running AD domain and certification services and one linux server (Srv-Lin-01 - 10.10.1.26/24). Also the external network (192.168.199.0/24) which provides internet connectivity. And a domain joined client (Clt-Win-01) which will run the VPN client to get access to the internal network.
Basic IP connectivity setup
The basic IP configuration of fortigate firewall is given below -
config system interface
edit "port1"
set vdom "root"
!!! Configure IP adress for external (internet) interface
set ip 192.168.199.121 255.255.255.0
set description "External"
set alias "External"
next
edit "port3"
set vdom "root"
!!! Configure IP adress for internal (LAN) interface
set ip 10.10.1.1 255.255.255.0
set description "Internal"
set alias "Internal"
next
end
config router static
edit 1
!!! Configure default gateway
set status enable
set dst 0.0.0.0 0.0.0.0
set gateway 192.168.199.2
set distance 10
set device "port1"
next
end
config system zone
!!! Creating firewall zones which will be used in firewall policies
edit "Zone-Internal"
set interface "port3"
next
edit "Zone-External"
set interface "port1"
next
edit "Zone-SSL-VPN"
set interface "ssl.root"
next
end
config firewall policy
!!! Firewall policy to allow LAN network internet access
edit 1
set srcintf "Zone-Internal"
set dstintf "Zone-External"
set action accept
set srcaddr "Net-10.10.1.0/24"
set dstaddr "all"
set schedule "always"
set service "ALL"
set nat enable
next
end
CA Certificate Installation
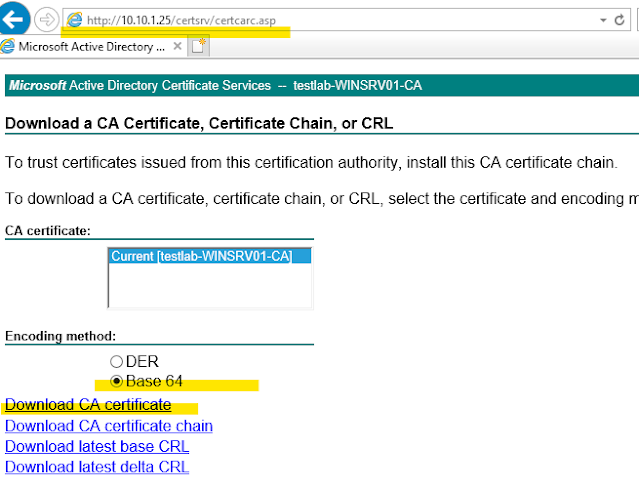
We need to download the CA certificate from the server (Srv-Win-Ad-01) and upload it to the firewall. CA certificate is needed because - our fortigate firewall will trust certificates issued by the CA server and our client computers will use certificates issued by the CA server for SSL-VPN authentication.
We go to - http://10.10.1.25/certsrv and download the CA certificate in "Base 64" format.
02 - Windows CA Certificate Download
We can open this certificate file with any text editor and copy/paste the certificate content into fortigate cli to upload it.
Fw-FGT-01 # config vpn certificate ca
Fw-FGT-01 (ca) # edit CA-Cert-Srv-Win-Ad-01
!!! Actual certificate content is not shown
Fw-FGT-01 (CA-Cert-Srv-Win-~-01) # set ca "-----BEGIN CERTIFICATE-----
aAJKSHjahskcbzxnmcbhjgsdhgashjdghjasgdhjasgjdhandbnvzxbncvzcxvbnzv
-----END CERTIFICATE-----"
Fw-FGT-01 (CA-Cert-Srv-Win-~-01) # end
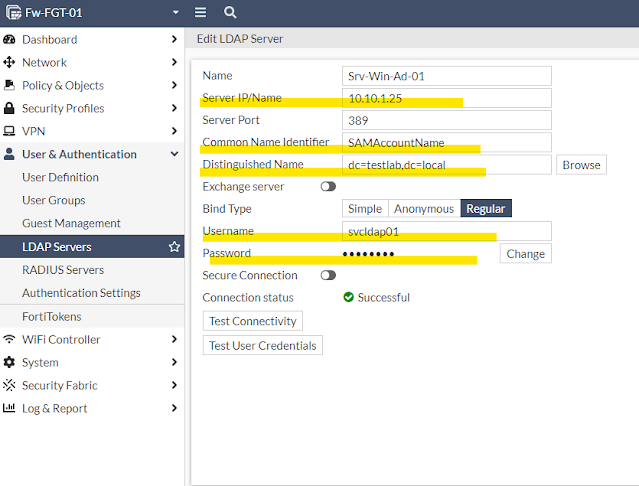
LDAP Server Configuration
The definition of LDAP server in fortigate firewall looks as below -
03 - LDAP Server Configuration
The equivalent configuration from the CLI -
config user ldap
edit "Srv-Win-Ad-01"
!!! AD-DC server IP address
set server "10.10.1.25"
set cnid "SAMAccountName"
!!! Our domain name is - testlab.local
set dn "dc=testlab,dc=local"
set type regular
!!! A service user account which can run query against AD-Domain
set username "svcldap01"
set password test123
next
end
PKI and LDAP SSL VPN User Group Configuration
We need to configure a PKI peer for certificate authentication which can be done from the CLI only.
config user peer
edit "SSL-Cert-Peer"
!!! Client certificates required to be signed by the CA server
set ca "CA-Cert-Srv-Win-Ad-01"
!!! Match certificate's UserPrincipalName to LDAP server's object
set ldap-server "Srv-Win-Ad-01"
set ldap-mode principal-name
!!! An optional parameter; if we want both certificate and username/password authentication. In our case two-factor is disabled.
set two-factor disable
next
end
After configuring the PKI peer; fortigate displays the information in GUI -
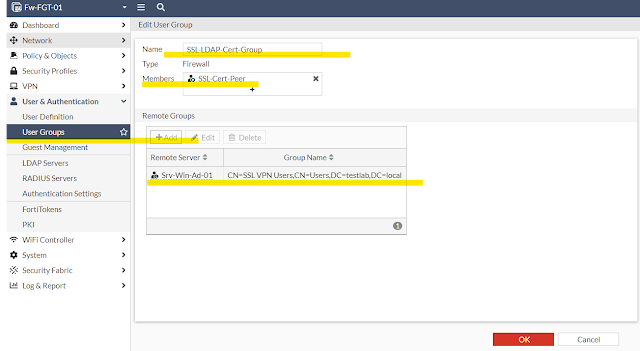
In the AD-Domain; we have a user group named "SSL VPN Users". A user must belong to this group to be able to connect via SSL VPN. We will add this user group in the firewall and associate it with our PKI peer.
The CLI commands to configure the equivalent is -
config user group
edit "SSL-LDAP-Cert-Group"
!!! Associate the PKI peer
set member "Srv-Win-Ad-01" "SSL-Cert-Peer"
config match
edit 1
!!! Selecting the AD/LDAP server
set server-name "Srv-Win-Ad-01"
!!! Selecting the group from AD/LDAP Server
set group-name "CN=SSL VPN Users,CN=Users,DC=testlab,DC=local"
next
end
next
end
SSL VPN Configuration
Fortigate firewall provides a lot of options to configure SSL VPN. For my setup I will use the following parameters -
- Web-mode/Tunnel-mode - We will not configure SSL VPN in web-mode. Only tunnel-mode will be configured.
- SSL-VPN Realms - We will configure realms which in our setup is used to separate username/password and certificate authentication mechanism.
- Split-tunneling - We will be using split-tunneling based on Policy Destination which means only networks that is used in firewall policy as destination will be pushed towards VPN clients.
- SSL-VPN client IP addressing - VPN clients will be assigned IP adress from network 10.10.4.0/24.
Let's dive into the configuration part -
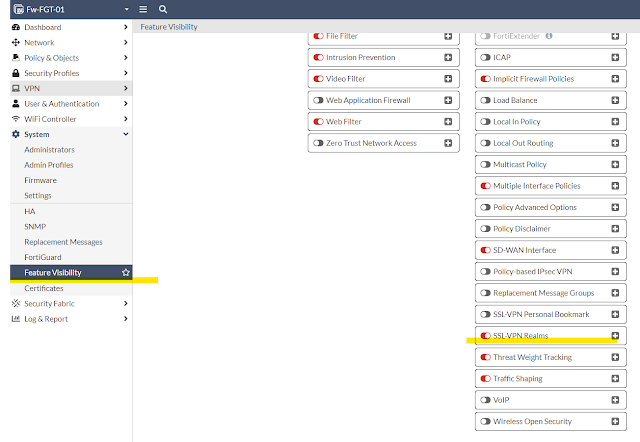
We need to enable SSL-VPN Realms which is disabled by default.
config system settings
!!! Enable SSL-VPN realm feature
set gui-sslvpn-realms enable
end
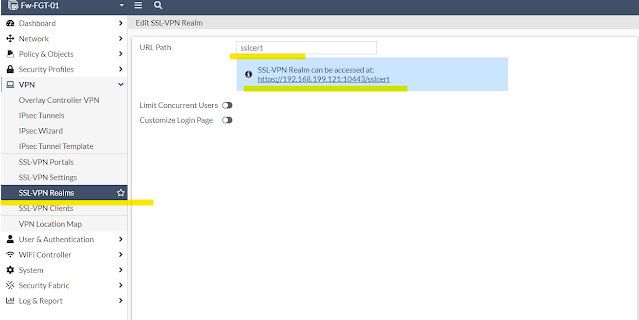
Now we will configure a realm named - sslcert ;
07 - Configure SSL-VPN LDAP Realms
config vpn ssl web realm
!!! A realm named sslcert is created
edit "sslcert"
next
end
Now we will create two portal named - Portal-LDAP-Cert (used for certificate authentication) and No-Access (used for deny default access with SSL-VPN).
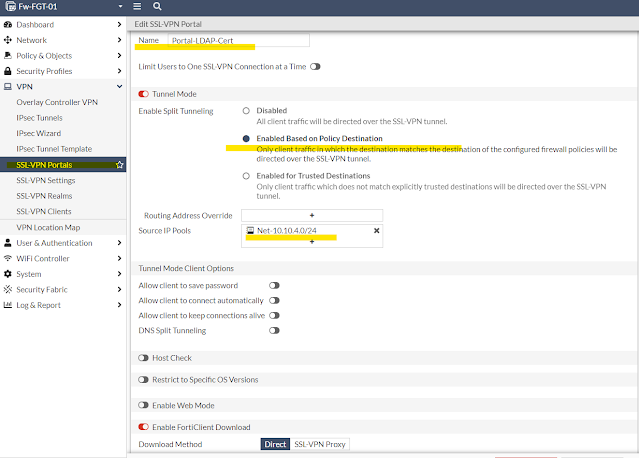
08 - SSL-VPN Portal for Certificate Authentication
config vpn ssl web portal
edit "Portal-LDAP-Cert"
!!! Only tunnel-mode is allowed
set tunnel-mode enable
!!! SSL-Client IP addressing
set ip-pools "Net-10.10.4.0/24"
!!! DNS server and suffix settings for clients
!!! Must configure from CLI
set dns-server1 10.10.1.25
set dns-suffix "testlab.local"
next
edit "No-Access"
!!! Both tunnel and web mode is disabled to prevent default access to VPN
set forticlient-download disable
next
end
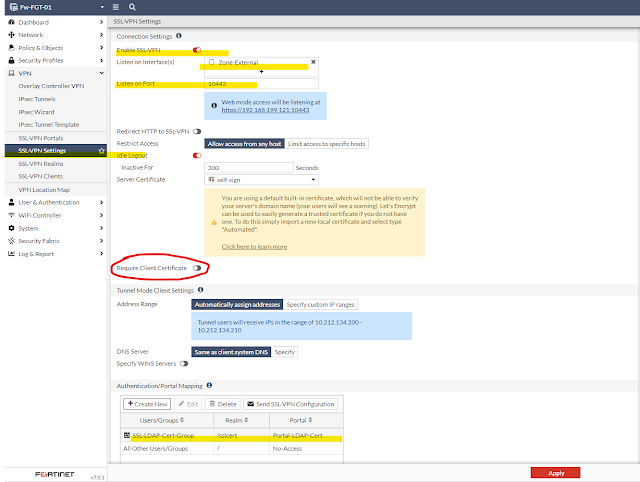
Now we will bind everything together under SSL-VPN settings. For certificate authentication we will not use "Require Client Certificate" under SSL-VPN Settings in GUI. Instead we will enable client-cert under authentication-rule which must be configured from the CLI.
config vpn ssl settings
set servercert "self-sign"
!!! Which Zone/Interface will listen for incoming SSL-VPN client requests
set source-interface "Zone-External"
!!! SSL-VPN will listen on port 10443
set port 10443
!!! Deny default access
set default-portal "No-Access"
config authentication-rule
edit 1
!!! user-group, portal and realm binding
set groups "SSL-LDAP-Cert-Group"
set portal "Portal-LDAP-Cert"
set realm "sslcert"
!!! Enable certificate authentication for clients
!!! Must be enabled from the CLI
set client-cert enable
next
end
end
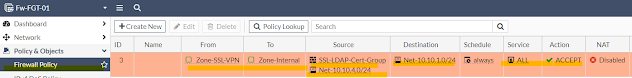
Last but not least we must have firewall policy which allows traffic from SSL-VPN client network to LAN (internal) network.
Now we have all the pieces in place for SSL-VPN configuration in a fortigate firewall.
Certificate Configuration (Client Computer)
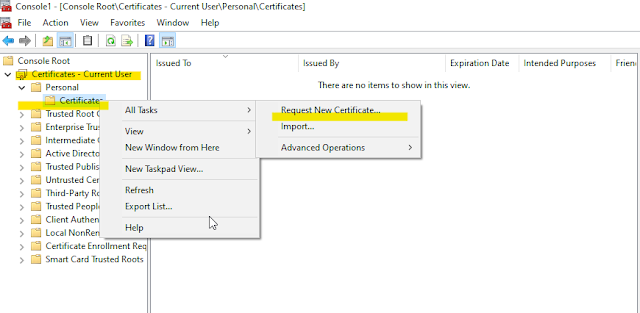
We will request a user-certificate from the CA server for our AD-Domain user named - "duser01".
After successful user-certificate enrollment the following will be displayed -
12 - Installed User Certificate from CA Server
FortiClient Configuration (SSL-VPN Client)
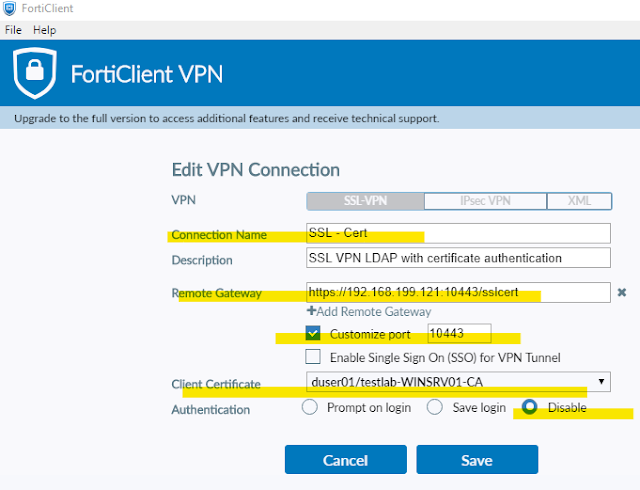
Now will install FortiClient in our client PC named Clt-Win-01 and configure it as below -
13 - FortiClient Settings for Certificate Authentication
SSL-VPN Verification
Now we will connect to the VPN and do some verification.
Let's do it from the client side first -
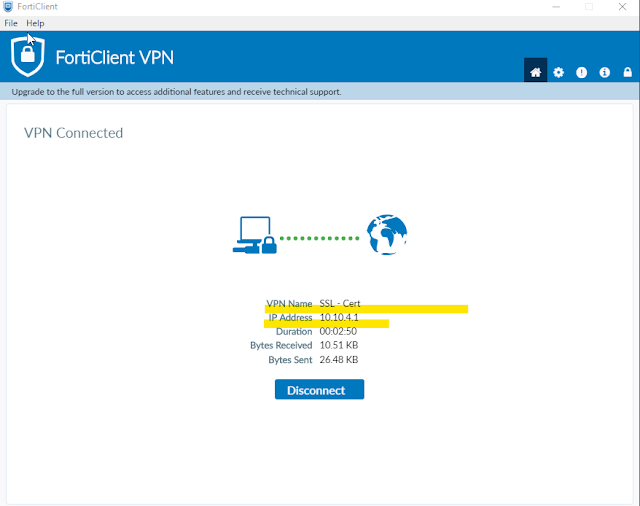
After successfully connecting to the VPN; the status window of FortiClient looks like below -
14 - FortiClient VPN Status
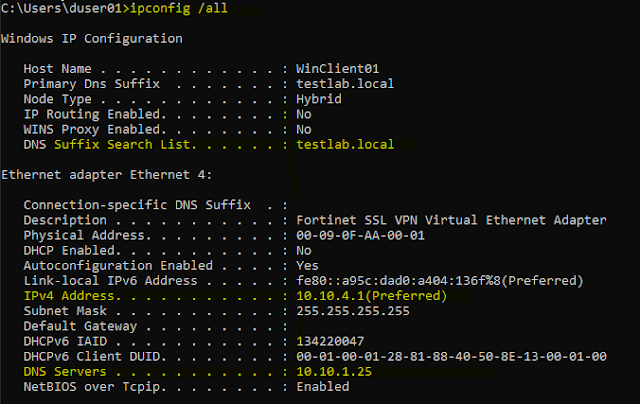
15 - VPN Client Interface Status
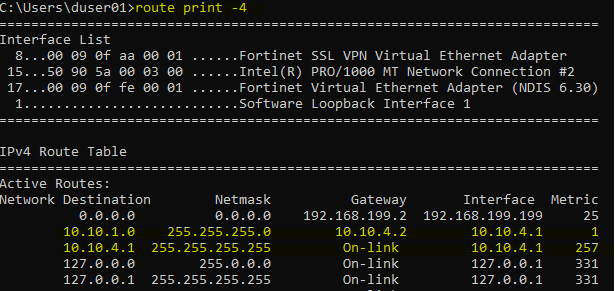
16 - VPN Client Routing Status
From above screenshots we can see that our client received IP address 10.10.4.1, DNS-suffix - testlab.local and DNS-server 10.10.1.25 after connecting to the VPN. And a routing table entry for 10.10.1.0/24 (internal network) is also created in the routing table.
Now we will do the verification from the firewall side -
Fw-FGT-01 # get vpn ssl monitor
SSL-VPN Login Users:
Index User Group Auth Type Timeout Auth-Timeout From HTTP in/out HTTPS in/out Two-factor Auth
0 SSL-Cert-Peer,cn=Users SSL-LDAP-Cert-Group 32(1) 253 28224 192.168.199.199 0/0 0/0 1
SSL-VPN sessions:
Index User Group Source IP Duration I/O Bytes Tunnel/Dest IP
0 SSL-Cert-Peer,cn=Users SSL-LDAP-Cert-Group 192.168.199.199 575 47130/32953 10.10.4.1
From above we can see that from external IP address 192.168.199.199, PKI peer named SSL-Cert-Peer from group SSL-LDAP-Cert-Group has connected to the VPN and assigned an IP adress 10.10.4.1 from the VPN subnet.
We can also do SSL-VPN debugging -
Fw-FGT-01 # diagnose debug application sslvpn -1
Debug messages will be on for 30 minutes.
Fw-FGT-01 # diagnose debug enable (output truncated)
[137:root:10]tunnelEnter:510 0x7fefa6b8f200:0x7fefa6c11c00 sslvpn user[SSL-Cert-Peer,cn=Users],type 32,logintime 0 vd 0
[137:root:10]sconn 0x7fefa6b8f200 (0:root) vfid=0 local=[192.168.199.121] remote=[192.168.199.199] dynamicip=[10.10.4.1]
[137:root:10]Will add auth policy for policy 3 for user SSL-Cert-Peer,cn=Users:SSL-LDAP-Cert-Group
[137:root:10]Add auth logon for user SSL-Cert-Peer,cn=Users:SSL-LDAP-Cert-Group, matched group number 1
[137:root:0]SND: IPCP Configure_Request id(1) [IP_Address 192.168.199.121]
[137:root:0]RCV: IPCP Configure_Request id(0) [IP_Address 0.0.0.0] [Primary_DNS_IP_Address 0.0.0.0] [Secondary_DNS_IP_Address 0.0.0.0]
[137:root:0]ipcp: returning Configure-NAK
[137:root:0]SND: IPCP Configure_Nak id(0) [IP_Address 10.10.4.1] [Primary_DNS_IP_Address 10.10.1.25] [Secondary_DNS_IP_Address 10.10.1.25]
We can also debug fortigate authentication daemon to observe how certificate authentication is working -
Fw-FGT-01 # diagnose debug application fnbamd -1
Debug messages will be on for 30 minutes.
Fw-FGT-01 # diagnose debug enable (output truncated)
931] __fnbamd_cert_auth_run-Exit, req_id=2072278661
[1643] __auth_cert_session_done-id=2072278661
[1608] auth_cert_success-id=2072278661
[1031] fnbamd_cert_auth_copy_cert_status-req_id=2072278661
[1040] fnbamd_cert_auth_copy_cert_status-Matched peer user 'SSL-Cert-Peer'
[834] fnbamd_cert_check_matched_groups-checking group with name 'SSL-LDAP-Cert-Group'
[121] fnbamd_ldap_dn_match-DN 'CN=SSL VPN Users,CN=Users,DC=testlab,DC=local' is matched with 'CN=SSL VPN Users,CN=Users,DC=testlab,DC=local', idx=0.
[896] fnbamd_cert_check_matched_groups-matched
To see the list of currently authenticated users in the firewall -
Fw-FGT-01 # diagnose firewall auth list
10.10.4.1, SSL-Cert-Peer,cn=Users
type: fw, id: 0, duration: 630, idled: 137
expire: 28661, allow-idle: 28799
flag(80): sslvpn
server: Srv-Win-Ad-01
packets: in 61 out 106, bytes: in 11712 out 19725
group_id: 3
group_name: SSL-LDAP-Cert-Group
----- 1 listed, 0 filtered ------
In above I have shown how to configure SSL-VPN with fortigate firewall and user-certificate as authentication mechanism. For username/password based SSL-VPN configuration look at my other blog.






Comments
Post a Comment