Network Device Configuration Templating with YAML, Jinja2, Python and Ansible
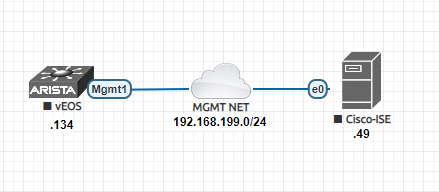
It was long time I had some fun writing some programming code. The other day I was thinking about one of my daily assignment as a network engineer - configuring network devices. Most of the time when we configure a network device - we start from a predefined configuration template which is copied from an existing device (the actual configuration) ; then open it in a text editor and do a search and replace operation to change the configuration according to the new device and it's configurations. What is wrong with this approach? First of all most of the time there is a risk that we will forget to change something; because we are doing a search and replace in a text editor and we have not made a list what are the things/configurations only need to change. Secondly there is no reusability; every time I need to open this text file and make changes by hand. Let's think for a moment. What are the things we actually change - when we configure a new device from an existing configurat