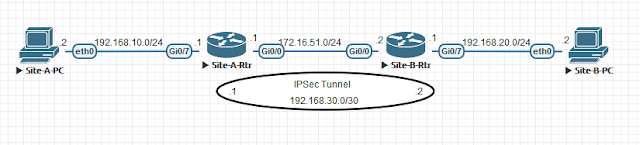
IPSec (tunnel mode) Site-To-Site VPN (IKE V2) between two Cisco routers with dynamic routing (OSPF)

Now comes the next part in IPSec series. This time we will configure IPSec VPN between two Cisco routers. For phase-1 our underlying protocol will be IKEV2 and IPSec will be run in tunnel mode. And we will do the routing by using OSPF protocol. Let's move on to our network topology - IPSec Tunnel Mode with IKEv2 and OSPF Even though the topology is straight forward, let's have a look at it. Traffic from 192.168.10.0/24 to 192.168.20.0/24 and vice versa will be encrypted by IPSec. For this example, we will assign IP address to our tunnel interface or VTIs. 192.168.30.0/30 network is reserved for that purpose. Then we have a loopback interface in each router which will be used as OSPF router-id. Site-A-Rtr configuration Assign IP address to the physical interface and loopback interface. interface GigabitEthernet0/0 ip address 172.16.51.1 255.255.255.0 ! interface GigabitEthernet0/7 ip address 192.168.10.1 255.255.255.0 ! interface Loop