Stacking switches Part - IV (Aruba CX Switch VSX - Virtual Switching Extension)
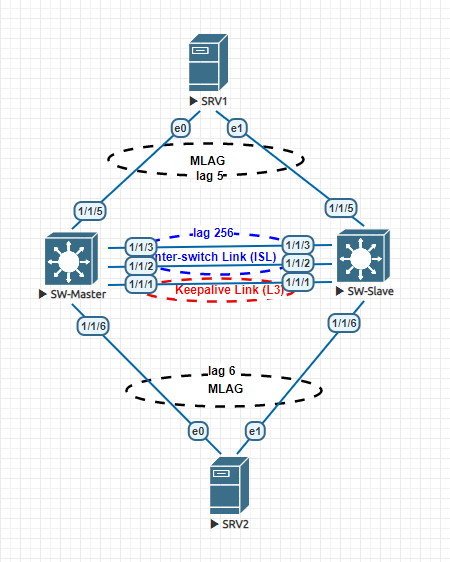
There is a new switching family released by HPE under the brand name Aruba CX series switches. These switches supports stacking in the form of MLAG. Today we will look at how to configure MLAG (multi chassis link aggregation) between two Aruba CX series switches. Aruba calls their implementation of mlag - Virtual Switching Extension (VSX) . Let's look at our network topology - Two Aruba CX switches will run peering between them and will form MLAG. Two Debian 10 linux machine will form multichassis link-aggregation with Aruba switches. They will simulate the client connection. Our topology looks like below - Aruba CX MLAG Topology Let's have a look at some terminology first before start configuring VSX. We need to define one switch as Master and another switch as Slave. VSX is an active-active forwarding solution, but the roles of master and slave is required. The purpose of that is during a VSX split, only the master will forward traffic and it will d...
