Cisco ASA AnyConnect vpn configuration with local authentication and vpn filter
In this blog post, we will configure Cisco ASA firewall AnyConnect VPN. Remote users will be authenticated against ASA's local user database to get access to the VPN and traffic filtering/firewalling will be done using a vpn filter in ASA.
Let's as usual introduce our topology -
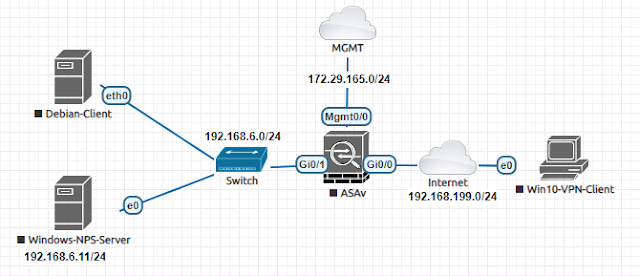 |
| 01 - AnyConnect VPN Topology |
The topology is straight forward. We have a inside network (192.168.6.0/24). Outside network is 192.168.199.0/24 where the ASA listens for anyconnect connections. And a management network 172.29.165.0/24 which is just a out-of-band management network for ASA.
We have a Win10-VPN-Client which will try to connect to inside network through anyconnect vpn. Debian-Client is just a client device in inside network to verify vpn connectivity. And Windows-NPS-Server is a radius server running NPS service. In this blog this nps server is not used. It will be used in the next blog when we move from local to radius authentication and vpn filter to dynamic acl.
Basic network connectivity configuration
Let's look at our interface and it's related IP configuration -
# show running-config interface
!
interface GigabitEthernet0/0
nameif outside
security-level 0
ip address dhcp setroute
!
interface GigabitEthernet0/1
nameif inside
security-level 100
ip address 192.168.6.1 255.255.255.0
!
interface Management0/0
no management-only
nameif mgmt
security-level 0
ip address dhcp
AnyConnect VPN configuration
We will activate a feature in the ASA so that our vpn traffic is not subjected to ASA's firewall inspection. Our vpn traffic will not be inspected by asa firewall. Instead it will be inspected by a vpn filter in ASA. Experienced ASA administrators knows about this feature; otherwise the readers can google about it to know more details.
!!! VPN traffic bypasses ASA firewall, instead will be inspected by a vpn filter
(config)# sysopt connection permit-vpn
We will use a redirect from http to https so that VPN users see our anyconnect web page only in https.
(config)# http redirect outside 80
We will use strong security protocol suites on our vpn connection. We will only accept tlsv1.2 or dtlsv1.2 and use higher encryption cipher suite. This step is optional; but highly recommended.
!!! Activating only most secured options for creating tunnel over https/ssl protocol
ssl client-version tlsv1.2
ssl server-version tlsv1.2 dtlsv1.2
ssl cipher dtlsv1.2 high
ssl cipher tlsv1.2 high
Then we will enable anyconnect vpn on the outside interface -
webvpn
!!! Users can download anyconnect client package, when they connect to VPN web page.
anyconnect image disk0:/anyconnect-win-4.9.01095-webdeploy-k9.pkg
!!! Outside interface will listen for anyconnect connection
enable outside
!!! Finally we enable anyconnect
anyconnect enable
!!! Optional command, when we want to allow users to select a user group alias when logging through web browser.
tunnel-group-list
enable
We need an IP pool from where our successful authenticated users will be assigned an IP adress.
!!! Anyconnect users will get an IP adress from the pool below
ip local pool anyvpn-pool 192.168.7.101-192.168.7.200 mask 255.255.255.0
We will use split tunneling for our vpn. Only required networks will be tunneled through the VPN. For example, a remote user internet access will be done still through his local ISP, will not be routed through the VPN. In our case, we will only tunnel network traffic to our inside network (192.168.6.0/24).
!!! Only traffic to 192.168.6.0/24 is routed through the VPN
access-list split-networks standard permit 192.168.6.0 255.255.255.0
Now we will create a vpn filter which is basically a acl/firewall which defines what kind of traffic is allowed and not allowed for anyconnect remote users.
!!! Only icmp to inside network and ssh to Debian-Client is allowed. All other traffic is denied through anyconnect vpn.
access-list anyvpn-filter extended permit icmp any 192.168.6.0 255.255.255.0
access-list anyvpn-filter extended permit tcp any host 192.168.6.5 eq ssh
access-list anyvpn-filter extended deny ip any any log
Now we will define a group policy for the vpn -
group-policy anyvpn-local-group-policy internal
group-policy anyvpn-local-group-policy attributes
!!! We will just activate vpn with anyconnect client. Client-less access through web browser is not allowed.
vpn-tunnel-protocol ssl-client
!!! We are doing split tunneling, only networks defined by split-networks will be tunneled through the vpn.
split-tunnel-policy tunnelspecified
split-tunnel-network-list value split-networks
!!! Only one simultaneous login is allowed.
vpn-simultaneous-logins 1
!!! No activity from the client within last 5 minutes, vpn will be terminated automatically.
vpn-idle-timeout 5
!!! Traffic through vpn will be subjected for inspection to a acl named anyvpn-filter.
vpn-filter value anyvpn-filter
!!! Define dns server and domain suffix for the vpn client.
dns-server value 8.8.8.8
default-domain value family.local
webvpn
anyconnect dpd-interval gateway 300
anyconnect dpd-interval client 300
!!! Setting mtu for anyconnect to avoid fragmentation
anyconnect mtu 1400
!!! When a user connects to the vpn adress from a web browser, it shows an option to download the vpn client.
anyconnect ask enable default anyconnect
!!! When a user disconnects from the vpn, the client remains installed.
anyconnect keep-installer installed
If any one is interested in running anyconnect through vpn client and also web browser, and tunnel all traffic through the vpn, they can change their settings as below. In our case, we are not using those settings.
group-policy anyvpn-local-group-policy attributes
vpn-tunnel-protocol ssl-client ssl-clientless
split-tunnel-policy tunnelall
Now we will bind everything together with a tunnel group -
tunnel-group anyvpn-local-tunnel-group type remote-access
tunnel-group anyvpn-local-tunnel-group general-attributes
!!! Binding the group policy
default-group-policy anyvpn-local-group-policy
!!! Binding the IP Pool
address-pool anyvpn-pool
tunnel-group anyvpn-local-tunnel-group webvpn-attributes
!!! We will use url to select different groups. If we want to connect as a local authenticated user we will below url as our vpn connection string.
group-url https://192.168.199.170/local enable
!!! This local authenticated group has a alias named "anyvpn-local-users" which is showed when we use web browser.
group-alias anyvpn-local-users enable
Last not least, we need to create a local user in the ASA which is allowed to log in through anyconnect vpn.
username testvpnlocal password testvpnlocal
username testvpnlocal attributes
service-type remote-access
!!! Binding the group policy with user profile
vpn-group-policy anyvpn-local-group-policy
At last we are done. Let's go to verification.
Verification
In our Win10-VPN-Client computer, if we open a web browser and go to 192.168.199.170 and after successful login, we will only get the option to download the vpn client from the ASA -
We have downloaded the client and installed it. Now we will try to connect through the anyconnect client -
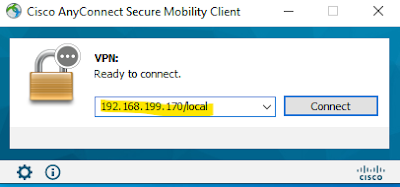 |
| 03 - AnyConnect login with vpn client |
Look at the connection string, it is same as the url defined in our tunnel group. After entering our credentials, we will be connected with the vpn.
Now we will have a look at the client's IP settings and routing table.
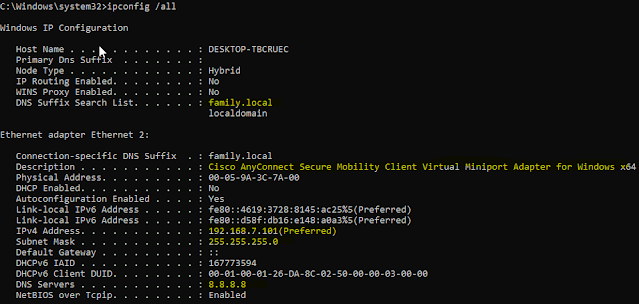 |
| 04 - AnyConnect client IP settings |
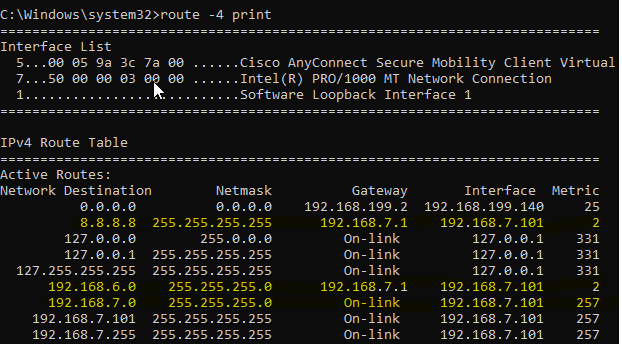
And the routing table -
We can see from the routing table that dns address (8.8.8.8/32) and ASA's inside network (192.168.6.0/24) is routed through the tunnel.
Now we will try to do ssh to the Debian-Client (192.168.6.5) and we can login successfully -
C:\Windows\system32>ssh root@192.168.6.5
root@192.168.6.5's password:
Linux deb10 4.19.0-10-amd64 #1 SMP Debian 4.19.132-1 (2020-07-24) x86_64
But if we want to do a rdp towards Windows-NPS-Server (192.168.6.11), it will not work and this event will be logged in ASA.
Now verify from the ASA -
Below command has long output, I am showing only the interested part -
# show vpn-sessiondb detail anyconnect
..Session Type: AnyConnect Detailed
Username : testvpnlocal Index : 2
Assigned IP : 192.168.7.101 Public IP : 192.168.199.140
Protocol : AnyConnect-Parent SSL-Tunnel DTLS-Tunnel
License : AnyConnect Premium
Encryption : AnyConnect-Parent: (1)none SSL-Tunnel: (1)AES-GCM-256 DTLS-Tunnel: (1)AES-GCM-256
Hashing : AnyConnect-Parent: (1)none SSL-Tunnel: (1)SHA384 DTLS-Tunnel: (1)SHA384
Group Policy : anyvpn-local-group-policy
Tunnel Group : anyvpn-local-tunnel-group
Login Time : 20:52:45 UTC Sun Sep 13 2020
SSL-Tunnel:
Tunnel ID : 2.2
Assigned IP : 192.168.7.101 Public IP : 192.168.199.140
Encryption : AES-GCM-256 Hashing : SHA384
Ciphersuite : ECDHE-ECDSA-AES256-GCM-SHA384
Encapsulation: TLSv1.2 TCP Src Port : 49903
TCP Dst Port : 443 Auth Mode : userPassword
Idle Time Out: 5 Minutes Idle TO Left : 0 Minutes
Client OS : Windows
Client Type : SSL VPN Client
Client Ver : Cisco AnyConnect VPN Agent for Windows 4.9.01095
Filter Name : anyvpn-filter
From above output we can see that, all the necessary settings are applied to client - group-policy, tunnel-group and vpn-filter.
And in ASA's log we will also found that from vpn client 192.168.7.101 to 192.168.6.11, rdp was denied.
Sep 13 2020 21:20:38: %ASA-6-106102: access-list anyvpn-filter denied tcp for user 'testvpnlocal' outside/192.168.7.101(50048) -> inside/192.168.6.11(3389) hit-cnt 1 first hit [0x82d7122d, 0x0]
That's about it - How to configure anyconnect vpn with local authentication and vpn filter.
In the next blog, we will look at how to configure anyconnect vpn with radius authentication and dynamic acl from radius server.




Comments
Post a Comment