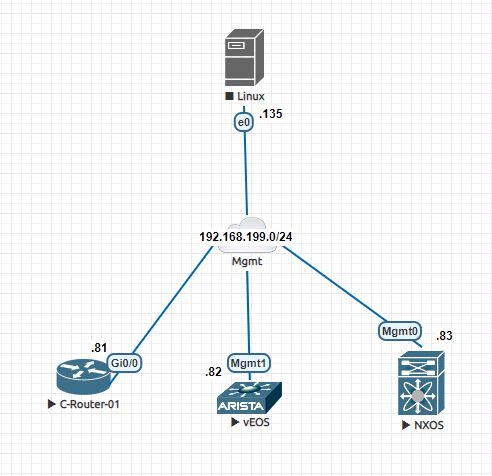
OSPF routing with GRE over Wireguard with VyOS router

Today we will have a look at how to run dynamic routing protocol over Wireguard. Due to some design choices how Wireguard works, there is no good mechanism of running directly dynamic protocols like OSPF over Wireguard tunnels when more than two (2) sites are involved in the routing domain. Readers are welcome to have a look at this to know more about about it and the warning - Warning: The protocol design of WireGuard requires that 'allowed-ips' must not overlap on a single interface. To add another OSPF link to the server, you will need to create wg02 on a different port. Instead we will use our good old friend - GRE to the rescue. We will use the concept of passenger/carrier protocol. Routing or data traffic will be encapsulated in GRE (passenger), then it will be encrypted and carried by Wireguard to the final destination. When we are doing two levels of encapsulation, it was always better to know about the protocol overheads involved, so that we can avoid ...