!
!!!Assign the defined radius server to a "aaa group"
aaa group server radius nps-servers
!!!This is the name of the server we have defined
server name nps01
!!!For radius packets, the source address is switch MGMT address
!!!The MGMT address is 172.16.250.2
ip radius source-interface Vlan250
domain-stripping
Now we will enable 802.1X authentication at switch's global level.
!!!This command enables 802.1x at global level
dot1x system-auth-control
!
!!!We are enabling logging for 802.1X, for testing purposes (optional)
dot1x logging verbose
!
!!!We are enabling 802.1X authentication using,
!!! our radius server group named "nps-servers"
aaa authentication dot1x default group nps-servers
!
!!! If radius server will assigned VLAN, ACL etc. upon successful authentication,
!!! this command allows the switch to accept those parameters from radius
aaa authorization network default group nps-servers
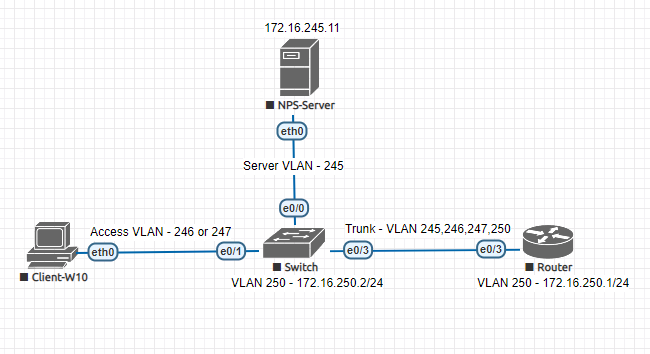
Now we will configure the switch port where the actual client is connected which is ethernet1/1. Let's discuss some behavior of an access port in Cisco's 802.1X implementation. In a Cisco switch, an access port where 802.1X is enabled, it disables the port's access until the switch has determined what to do with it by 802.1X. So, there will be no mac-address learning or any activity on the port until the port has gone through 802.1X authentication. Let's look at an example -
interface Ethernet1/1
switchport mode access
switchport access vlan 246
authentication port-control auto
dot1x pae authenticator
In above configuration, even though the port is placed in VLAN 246, it will not be granted access to the VLAN until it has passed 802.1X authentication. We will not see a mac-address associated with that port. If the client connected with the port passes authentication, we will see mac-address associated with that port.
Switch#sh interfaces ethernet 1/1 switchport
Name: Et1/1
Switchport: Enabled
Administrative Mode: static access
Operational Mode: static access
Administrative Trunking Encapsulation: negotiate
Operational Trunking Encapsulation: native
Negotiation of Trunking: Off
Access Mode VLAN: 246 (VLAN0246)
Trunking Native Mode VLAN: 1 (default)
Administrative Native VLAN tagging: enabled
Switch#sh mac address-table dynamic interface ethernet 1/1
Mac Address Table
-------------------------------------------
Vlan Mac Address Type Ports
---- ----------- -------- -----
Switch#
So, with Cisco if we define access vlan under interface configuration, that means client will be granted access to that VLAN upon successful authentication. And if we do not define any access VLAN under interface, then upon successful authentication, the port will assign it's VLAN from radius server. In our case we will use this variant, no access vlan under interface configuration, it will we assigned by the radius/NPS server.
Now we will configure 802.1X at interface level where the client is connected.
interface Ethernet1/1
!!!Port is not assigned to a access VLAN, VLAN is assigned by Radius.
switchport mode access
!!!802.1x usually configured on access ports.
!!! Enabling portfast will reduce STP convergence time of the port.
spanning-tree portfast
!!!Enables 802.1X for an interface
authentication port-control auto
dot1x pae authenticator
!!!If authentication fails, port is placed into vlan 247, default retry is 2 times
authentication event fail retry 2 action authorize vlan 247
!!!If radius server is not reachable, port is placed into vlan 247
authentication event server dead action authorize vlan 247
!!!After a radius server dead event, when the server comes backup again,
!!!initiates re-authentication of connected clients.
authentication event server alive action reinitialize
!!!If connected host is not running 802.1X client, port is placed into vlan 247
authentication event no-response action authorize vlan 247
!!!Only one device connected to the port, needs to pass authentication.
!!!Useful when we are running also VM, from the connected host.
authentication host-mode multi-host
!!!Enables periodic authentication which is triggered every 1 hour
authentication periodic
authentication timer reauthenticate 3600
dot1x timeout tx-period 10
dot1x timeout quiet-period 15
end
If required we can adjust different timers for authentication and 802.1X, their explanation is out of scope of this article -
Switch(config)#int e1/1
Switch(config-if)#authentication timer ?
inactivity Interval in seconds after which if there is no activity from
the client then it will be unauthorized (default OFF)
reauthenticate Time in seconds after which an automatic re-authentication
should be initiated (default 1 hour)
restart Interval in seconds after which an attempt should be made to
authenticate an unauthorized port (default 60 sec)
unauthorized Time in seconds after which an unauthorized session will get
deleted
Switch(config-if)#dot1x timeout ?
auth-period Timeout for authenticator reply
held-period Timeout for authentication retries
quiet-period QuietPeriod in Seconds
ratelimit-period Ratelimit Period in seconds
server-timeout Timeout for Radius Retries
start-period Timeout for EAPOL-start retries
supp-timeout Timeout for supplicant reply
tx-period Timeout for supplicant retries
Verification
If we have configured everything properly, then when we connect "Client-W10" with switch port "e1/1", we will see that Windows is asking for username/password. If we enter correct username/password, the port will be placed in vlan 246 (client vlan) and granted network access.
The below output are taken after a successful authentication event -
Switch#show dot1x
Sysauthcontrol Enabled
Dot1x Protocol Version 3
We can see an individual port's dot1x timers, EAP protocol used (PEAP), client's mac-address (5000.0004.0000), authentication state (AUTHENTICATED) etc. from the output below.
Switch#sh dot1x interface ethernet 1/1 details
Dot1x Info for Ethernet1/1
-----------------------------------
PAE = AUTHENTICATOR
QuietPeriod = 15
ServerTimeout = 0
SuppTimeout = 30
ReAuthMax = 2
MaxReq = 2
TxPeriod = 10
Dot1x Authenticator Client List
-------------------------------
EAP Method = PEAP
Supplicant = 5000.0004.0000
Session ID = AC10FA02000000120190D26E
Auth SM State = AUTHENTICATED
Auth BEND SM State = IDLE
By using command below we can find authentication information like, client's mac and ip address, username, server policies (radius assigned vlan) etc.
Switch#sh authentication sessions interface ethernet 1/1 details
Interface: Ethernet1/1
MAC Address: 5000.0004.0000
IPv6 Address: Unknown
IPv4 Address: 172.16.246.101
User-Name: user01
Status: Authorized
Domain: DATA
Oper host mode: multi-host
Oper control dir: both
Session timeout: 3600s (local), Remaining: 2295s
Timeout action: Reauthenticate
Restart timeout: N/A
Periodic Acct timeout: N/A
Session Uptime: 1422s
Common Session ID: AC10FA02000000120190D26E
Acct Session ID: Unknown
Handle: 0x3C000006
Current Policy: POLICY_Et1/1
Local Policies:
Service Template: DEFAULT_LINKSEC_POLICY_SHOULD_SECURE (priority 150)
Security Policy: Should Secure
Security Status: Link Unsecure
Server Policies:
Vlan Group: Vlan: 246
Method status list:
Method State
dot1x Authc Success
Now let's see what happens when authentication fails because of entering wrong username/password. We have entered an unknown user named "sdfsf", then from the output below we can see that port is placed in VLAN 247 by the switch (local policies), authentication has failed.
Switch#sh authentication sessions interface ethernet 1/1 details
Interface: Ethernet1/1
MAC Address: 5000.0004.0000
IPv6 Address: Unknown
IPv4 Address: 172.16.247.101
User-Name: sdfsf
Status: Authorized
Domain: UNKNOWN
Oper host mode: multi-host
Oper control dir: both
Session timeout: 3700s (local), Remaining: 3547s
Timeout action: Reauthenticate
Restart timeout: N/A
Periodic Acct timeout: N/A
Session Uptime: 159s
Common Session ID: AC10FA020000001401B1EA0A
Acct Session ID: Unknown
Handle: 0x22000008
Current Policy: POLICY_Et1/1
Local Policies:
Service Template: AUTH_FAIL_VLAN_Et1/1 (priority 150)
Vlan Group: Vlan: 247
Method status list:
Method State
dot1x Authc Failed
Important debug commands related to 802.1X are -
debug dot1x
debug authentication
debug radius
We can manually reset the authentication status of an interface -
Switch#clear authentication sessions interface ethernet 1/1
We can test whether a client connected to a switch port can has the necessary client software or EAPOL capable -
Switch#dot1x test eapol-capable interface ethernet 1/1
*Aug 4 17:18:13.843: %DOT1X-6-INFO_EAPOL_PING_RESPONSE: The interface Et1/1 has an 802.1x capable client with MAC 5000.0004.0000
We can also test the radius server connectivity and settings from the switch by commands -
Switch#show aaa servers
RADIUS: id 1, priority 1, host 172.16.245.11, auth-port 1812, acct-port 1813
State: current UP, duration 30683s, previous duration 0s
Dead: total time 0s, count 0
Quarantined: No
Authen: request 0, timeouts 0, failover 0, retransmission 0
Response: accept 0, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Author: request 0, timeouts 0, failover 0, retransmission 0
Response: accept 0, reject 0, challenge 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Account: request 0, timeouts 0, failover 0, retransmission 0
Request: start 0, interim 0, stop 0
Response: start 0, interim 0, stop 0
Response: unexpected 0, server error 0, incorrect 0, time 0ms
Transaction: success 0, failure 0
Throttled: transaction 0, timeout 0, failure 0
Switch#test aaa group nps-servers user01 passWORD new-code
User successfully authenticated
USER ATTRIBUTES
service-type 0 2 [Framed]
tunnel-medium-type 0 6 [ALL_802]
tunnel-private-group 0 "246"
tunnel-type 0 13 [vlan]



Thank you for your articles that you have shared with us. Hopefully you can give the article a good benefit to us. Rekryteringskonsult i Sundsvall
ReplyDelete