In-depth look at Fortigate's ADVPN - Part I
This is the first part of a series where we will look at Fortigate's ADVPN (Auto Discovery VPN) implementation and how it works. As usual the question - what is ADVPN and why do we need it.
Let's do an example topology. We have a hub (Central/HQ site) and spoke (Branch site) consisting of 21 nodes (1+20). As this is a hub-and-spoke topology all the inter-site communication goes through Hub/Central site. All the traffic between sites is encrypted by IPSec. Now 21st site comes online. What we will need at least to connect this new spoke with the rest of the network is -
Let's do an example topology. We have a hub (Central/HQ site) and spoke (Branch site) consisting of 21 nodes (1+20). As this is a hub-and-spoke topology all the inter-site communication goes through Hub/Central site. All the traffic between sites is encrypted by IPSec. Now 21st site comes online. What we will need at least to connect this new spoke with the rest of the network is -
At the HUB -
- A new IPSec site-to-site tunnel configuration.
- New dynamic routing configuration so that hub can send and receive routing information to spoke.
- Firewall rules adjustments.
At the Spoke (new site)
- A new IPSec site-to-site tunnel configuration.
- New dynamic routing configuration so that spoke can send and receive routing information to hub.
- Firewall rules adjustments.
What if there is a configuration knob so that we can configure the Hub once and for all. That is every time a new spoke is joined to the network, we do not need to do anything at the Hub site, we just configure the spoke site. And yes that is possible by using Fortigate's dial-up IPSec VPN tunnels at the HUB site. In part I we will look at that. And in part II we will look at how to convert this hub-spoke topology, to a full mesh topology (ADVPN) without much configuration efforts.
All the configuration in this example is done using FortiOS version 6.2. Our example will use Fortigate's new dial-up logic. As there was a major change done by Fortinet how their dial-up IPSec VPN works, I recommend reading the documentation mentioned in the references section.
Topology
Let's introduce our topology -
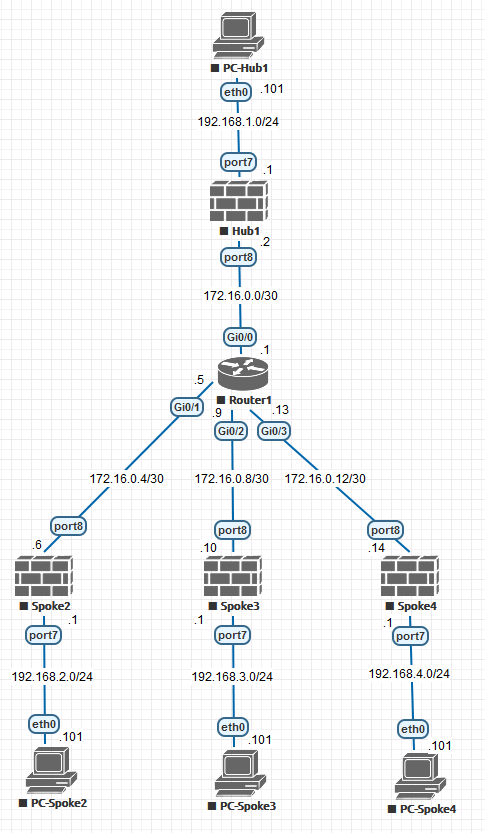 |
| ADVPN Physical Topology |
We have a hub site and three spoke sites. Our goal is two configure a dial-up IPSec VPN (server) at the Hub so that we do not need to do any configuration when a new Spoke joins to the network. We will just configure IPSec and routing at the spoke site. And that's it. Fortigate's dial-up logic will take care of the rest.
The IP adressering is given in the table below -
The IP adressering is given in the table below -
Site
|
WAN
|
LAN
|
IPSec Tunnel
|
Loopback
|
Hub1
|
172.16.0.2/30
|
192.168.1.1/24
|
192.168.10.1/24
|
192.168.0.1/32
|
Spoke1
|
172.16.0.6/30
|
192.168.2.1/24
|
192.168.10.2/24
|
192.168.0.2/32
|
Spoke2
|
172.16.0.10/30
|
192.168.3.1/24
|
192.168.10.3/24
|
192.168.0.3/32
|
Spoke3
|
172.16.0.14/30
|
192.168.4.1/24
|
192.168.10.4/24
|
192.168.0.4/32
|
Routing
We will use OSPF as the routing protocol between hub and spokes. We need to understand how our routing topology looks beforehand to understand why we are configuring certain things in OSPF. Below is an example of routing topology -
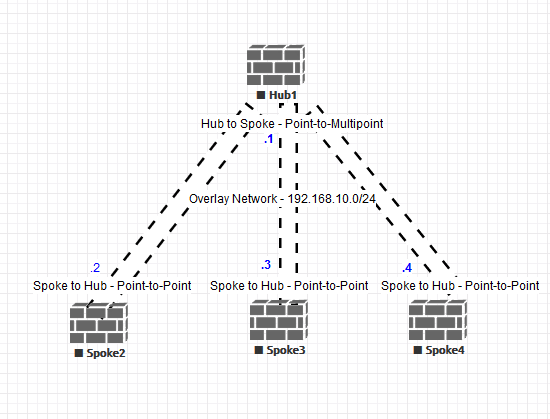 |
| ADVPN Routing Topology |
The most important thing here to understand is that the Hub sees the network as point-to-multipoint (Hub has one IPSec tunnel to each Spoke) and each Spoke sees the network as point-to-point (Spoke has IPSec tunnel only to the Hub). To run OSPF over those IPSec tunnels, both Hub and Spoke must find a way to tell each other what are their respective tunnel IP addresses. Fortigate overcomes this limitations by using proprietary adress exchanging mechanism during IPSec phase-1 negotiation (set exchange-interface-ip enable).
Enough talking, let's start configuring - (as most of things cannot be done from gui, we will configure the required configuration from cli).
Enough talking, let's start configuring - (as most of things cannot be done from gui, we will configure the required configuration from cli).
Hub1 Configuration
Let's look at Hub1's physical interface and IP address configuration
config system interface
!!!Lan facing interface
edit "port7"
set vdom "root"
set ip 192.168.1.1 255.255.255.0
set allowaccess ping
set type physical
set description "Lan"
set alias "Lan"
next
!!!Internet facing interface
edit "port8"
set vdom "root"
set ip 172.16.0.2 255.255.255.252
set allowaccess ping
set type physical
set description "Internet"
set alias "Internet"
next
!!!Loopback interface, used for router-id in OSPF
edit "Loopback"
set vdom "root"
set ip 192.168.0.1 255.255.255.255
set allowaccess ping
set type loopback
set description "Loopback"
set alias "Loopback"
set role lan
next
end
Now we will configure the IPSec phase-1 at the Hub1.
config vpn ipsec phase1-interface
edit "Hub1-Phase1"
set ike-version 2
set proposal des-md5
set dhgrp 5
set authmethod psk
set psksecret test123
set nattraversal disable
set keylife 86400
set dpd on-idle
set dpd-retrycount 3
set dpd-retryinterval 20
!!!Internet facing interface
set interface "port8"
!!!It is a dynamic (dial-up) tunnel which accepts negotiation from any spokes.
set type dynamic
set peertype any
!!!Activating fortigate's new dial-up logic
set net-device disable
!!!To find which tunnel to use when connecting to a spoke
set tunnel-search nexthop
!!!No reverse route injection, routing table will be built by routing protocol
set add-route disable
!!!During phase-1,the Hub1 exchange it's IPSec tunnel interface IP address with the Spoke.
set exchange-interface-ip enable
next
end
Next we will configure IPSec phase-2 at the Hub1.
config vpn ipsec phase2-interface
edit "Hub1-Phase2"
set encapsulation tunnel-mode
set proposal des-md5
set pfs disable
set keylife-type seconds
set keylifeseconds 43200
set keepalive disable
!!!Connecting phase-2 with phase-1
set phase1name "Hub1-Phase1"
next
end
As we will be running OSPF, we need to assign an IP adress to Hub1's IPSec tunnel interface. We have reserved 192.168.10.0/24 network as our overlay network. Every device participating in dial-up IPSec VPN will get an IP adress from this network for their tunnel interface.
config system interface
edit "Hub1-Phase1"
set vdom "root"
set ip 192.168.10.1 255.255.255.255
set allowaccess ping
set type tunnel
!!!In fortigate remote IP needs to an IP adress from 192.168.10.0/24 network.
!!!For clarity, in Hub we will use 192.168.10.254/24, an unused IP adress from overlay network.
!!!And in Spokes we will use Hub's tunnel IP as remote IP.
set remote-ip 192.168.10.254 255.255.255.0
set snmp-index 10
set interface "port8"
next
end
Now we will configure the firewall policies. Our policy is very simple - we will allow everything from Hub1's LAN to Spoke's LAN and vice versa. Also, we will allow traffic between Spokes which goes through the Hub.
For configuration flexibility we have assigned our interfaces to different zones which are pretty self-explanatory.
config system zone
edit "Lan-Zone"
set interface "port7"
next
edit "Vpn-Zone"
set interface "Hub1-Phase1"
next
edit "Internet-Zone"
set interface "port8"
next
end
config firewall policy
edit 1
set srcintf "Lan-Zone"
set dstintf "Vpn-Zone"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 2
set srcintf "Vpn-Zone"
set dstintf "Lan-Zone"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 3
!!!Allows traffic between spokes which goes through Hub1
set srcintf "Vpn-Zone"
set dstintf "Vpn-Zone"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
Now we will configure OSPF routing as below (remember Hub's OSPF interface is point-to-multipoint type - Hub1 connects to different Spokes).
config router ospf
!!!Loopback address is router-id
set router-id 192.168.0.1
config area
edit 0.0.0.0
next
end
config ospf-interface
edit "Hub1-Phase1"
!!!Tunnel interface will have some OSPF settings applied to it
set interface "Hub1-Phase1"
!!!OSPF network type will be point-to-multipoint
set network-type point-to-multipoint
!!!P-to-MP interface has a default hello interval of 30 sec and dead interval of 120 sec
!!!We will change it to 10 and 40 which is default equivalent of P-to-P interface.
!!!So, that hello and dead timers are consistent between Hub and Spoke
set dead-interval 40
set hello-interval 10
set mtu-ignore enable
next
end
config network
edit 1
!!!Advertising the loopback network
set prefix 192.168.0.1 255.255.255.255
next
edit 2
!!!Advertising the LAN/inside network
set prefix 192.168.1.0 255.255.255.0
next
edit 3
!!!Advertising the IPSec VPN/Overlay network
set prefix 192.168.10.0 255.255.255.0
next
end
end
Spoke2 configuration
As all the spokes has similar configuration, we will only show the configuration at Spoke2. For other spokes only the IP addresses changes.
Let's look at Spoke2's physical interface and IP address configuration -
config system interface
!!!Lan facing interface
edit "port7"
set vdom "root"
set ip 192.168.2.1 255.255.255.0
set allowaccess ping
set type physical
set description "Lan"
set alias "Lan"
next
!!!Internet facing interface
edit "port8"
set vdom "root"
set ip 172.16.0.6 255.255.255.252
set allowaccess ping
set type physical
set description "Internet"
set alias "Internet"
next
!!!Loopback interface, used for router-id in OSPF
edit "Loopback"
set vdom "root"
set ip 192.168.0.2 255.255.255.255
set allowaccess ping
set type loopback
set description "Loopback"
set alias "Loopback"
set role lan
next
end
Now we will configure the IPSec phase-1 at the Spoke2.
config vpn ipsec phase1-interface
edit "Spoke2-Phase1"
set ike-version 2
set proposal des-md5
set dhgrp 5
set authmethod psk
set psksecret test123
set nattraversal disable
set keylife 86400
set dpd on-idle
set dpd-retrycount 3
set dpd-retryinterval 20
!!!Internet facing interface
set interface "port8"!!!A spoke connects only to the Hub via IPSec.
!!!So, it will be static IPSec tunnel where it will connect to Hub's internet facing IP address.
set type static
set peertype any
set remote-gw 172.16.0.2
!!!As the spoke creates only P-to-P tunnel, no need to activate fortigate's new dial-up logic
set net-device enable
!!!During phase-1,the Spoke exchange it's IPSec tunnel interface IP address with the Hub.
set exchange-interface-ip enable
next
end
Next we will configure IPSec phase-2 at the Spoke2.
config vpn ipsec phase2-interface
edit "Spoke2-Phase2"
set encapsulation tunnel-mode
set proposal des-md5
set pfs disable
set keylife-type seconds
set keylifeseconds 43200
!!!Connecting phase-2 with phase-1
set phase1name "Spoke2-Phase1"
!!!The spoke will initiate the IPSec negotiation.
!!!The hub does not know the internet facing IP adress of the spokes beforehand.
!!!So, it is the responsibility of the spokes to initiate the IPSec negotiation.
!!!The hub acts as a responder in IPSec negotiation.
set auto-negotiate enable
next
end
As we will be running OSPF, we need to assign an IP adress to Spoke2's IPSec tunnel interface. We have reserved 192.168.10.0/24 network as our overlay network and Spoke2 will get an IP adress from this network.
config system interface
edit "Spoke2-Phase1"
set vdom "root"
set ip 192.168.10.2 255.255.255.255
set allowaccess ping
set type tunnel
!!!Remote IP is set to Hub1's tunnel IP address
set remote-ip 192.168.10.1 255.255.255.0
set interface "port8"
next
end
Now we will configure the firewall policies. Our policy is very simple - we will allow everything from Spoke2's LAN to Hub1's LAN or other Spokes LAN and vice versa. For configuration flexibility we have assigned our interfaces to different zones which are pretty self-explanatory.
config system zone
edit "Lan-Zone"
set interface "port7"
next
edit "Vpn-Zone"
set interface "Spoke2-Phase1"
next
edit "Internet-Zone"
set interface "port8"
next
end
config firewall policy
edit 1
set srcintf "Lan-Zone"
set dstintf "Vpn-Zone"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
edit 2
set srcintf "Vpn-Zone"
set dstintf "Lan-Zone"
set srcaddr "all"
set dstaddr "all"
set action accept
set schedule "always"
set service "ALL"
next
end
Now we will configure OSPF routing as below for Spoke2. By default tunnel interface created by IPSec is of type point-to-point. So, for Spoke2 we don't need to specify explicitly that OSPF sees tunnel interface as point-to-point. But we will do that here for configuration clarity and consistency.
config router ospf
!!!Loopback address is router-id
set router-id 192.168.0.2
config area
edit 0.0.0.0
next
end
config ospf-interface
!!!Tunnel interface will have some OSPF settings applied to it
edit "Spoke2-Phase1"
set interface "Spoke2-Phase1"
!!!OSPF network type will be point-to-point
set network-type point-to-point
set dead-interval 40set hello-interval 10
set mtu-ignore enable
next
end
config network
edit 1
!!!Advertising the loopback network
set prefix 192.168.0.2 255.255.255.255
next
edit 2
!!!Advertising the LAN/inside network
set prefix 192.168.2.0 255.255.255.0
next
edit 3
!!!Advertising the IPSec VPN/Overlay network
set prefix 192.168.10.0 255.255.255.0
next
end
end
That's it. We are done with Spoke2's configuration. Spoke3 and Spoke4 are also configured similarly.
Verification
From Hub1 if we use the below command we will see the following output. The output is very long, we have truncated the output with necessary information only.
Hub1 # diagnose vpn tunnel list
list all ipsec tunnel in vd 0
------------------------------------------------------
name=Hub1-Phase1_0 ver=2 serial=2 172.16.0.2:0->172.16.0.6:0 dst_mtu=1500
bound_if=10 lgwy=static/1 tun=intf/0 mode=dial_inst/3 encap=none/672 options[02a0]=search-nexthop rgwy-chg frag-rfc run_state=1 accept_traffic=1
parent=Hub1-Phase1 index=0
!!!Tunnel to Spoke2 with interface name Hub1-Phase1 and index 0
------------------------------------------------------
name=Hub1-Phase1_1 ver=2 serial=3 172.16.0.2:0->172.16.0.10:0 dst_mtu=1500
bound_if=10 lgwy=static/1 tun=intf/0 mode=dial_inst/3 encap=none/672 options[02a0]=search-nexthop rgwy-chg frag-rfc run_state=1 accept_traffic=1
parent=Hub1-Phase1 index=1
!!!Tunnel to Spoke3 with interface name Hub1-Phase1 and index 1
------------------------------------------------------
name=Hub1-Phase1_2 ver=2 serial=4 172.16.0.2:0->172.16.0.14:0 dst_mtu=1500
bound_if=10 lgwy=static/1 tun=intf/0 mode=dial_inst/3 encap=none/672 options[02a0]=search-nexthop rgwy-chg frag-rfc run_state=1 accept_traffic=1
parent=Hub1-Phase1 index=2
!!!Tunnel to Spoke4 with interface name Hub1-Phase1 and index 2
------------------------------------------------------
name=Hub1-Phase1 ver=2 serial=1 172.16.0.2:0->0.0.0.0:0 dst_mtu=0
bound_if=10 lgwy=static/1 tun=intf/0 mode=dialup/2 encap=none/544 options[0220]=search-nexthop frag-rfc accept_traffic=1
proxyid_num=0 child_num=3 refcnt=21 ilast=1669 olast=1669 ad=/0
stat: rxp=597 txp=621 rxb=72896 txb=51624
dpd: mode=on-idle on=0 idle=20000ms retry=3 count=0 seqno=0
natt: mode=none draft=0 interval=0 remote_port=0
run_tally=3
ipv4 route tree:
172.16.0.6 0
172.16.0.10 1
172.16.0.14 2
192.168.10.2 0
!!!OSPF finds Spoke1's tunnel IP adress by Hub1-Phase1 with index number 0
192.168.10.3 1
!!!OSPF finds Spoke2's tunnel IP adress by Hub1-Phase1 with index number 1
192.168.10.4 2
!!!OSPF finds Spoke3's tunnel IP adress by Hub1-Phase1 with index number 2
Hub1 # get router info ospf interface
Hub1-Phase1 is up, line protocol is up
Internet Address 192.168.10.1/24, Area 0.0.0.0, MTU 1446
Process ID 0, VRF 0, Router ID 192.168.0.1, Network Type POINTOMULTIPOINT, Cost: 100
Transmit Delay is 1 sec, State Point-To-Point
Timer intervals configured, Hello 10.000, Dead 40, Wait 40, Retransmit 5
Hello due in 00:00:08
Neighbor Count is 3, Adjacent neighbor count is 3
Crypt Sequence Number is 10
Hello received 661 sent 225, DD received 27 sent 26
LS-Req received 6 sent 6, LS-Upd received 22 sent 34
LS-Ack received 49 sent 0, Discarded 0
Routing table for VRF=0
!!! 192.168.0.X are Spokes's loopback network
O 192.168.0.2/32 [110/200] via 192.168.10.2, Hub1-Phase1, 00:22:25
O 192.168.0.3/32 [110/200] via 192.168.10.3, Hub1-Phase1, 00:20:55
O 192.168.0.4/32 [110/200] via 192.168.10.4, Hub1-Phase1, 00:20:45
!!! 192.168.X.0/24 are Spoke's LAN networks
O 192.168.2.0/24 [110/101] via 192.168.10.2, Hub1-Phase1, 00:22:25
O 192.168.3.0/24 [110/101] via 192.168.10.3, Hub1-Phase1, 00:20:55
O 192.168.4.0/24 [110/101] via 192.168.10.4, Hub1-Phase1, 00:00:19
Now verification from Spoke2. It has only one IPSec tunnel to Hub1.
Spoke2 # diagnose vpn tunnel list
list all ipsec tunnel in vd 0
------------------------------------------------------
name=Spoke2-Phase1 ver=2 serial=1 172.16.0.6:0->172.16.0.2:0 dst_mtu=1500
bound_if=10 lgwy=static/1 tun=intf/0 mode=auto/1 encap=none/528 options[0210]=create_dev frag-rfc accept_traffic=1
Spoke2 # get router info ospf interface
Spoke2-Phase1 is up, line protocol is up
Internet Address 192.168.10.2/24, Area 0.0.0.0, MTU 1446
Process ID 0, VRF 0, Router ID 192.168.0.2, Network Type POINTOPOINT, Cost: 100
Transmit Delay is 1 sec, State Point-To-Point
Timer intervals configured, Hello 10.000, Dead 40, Wait 40, Retransmit 5
Hello due in 00:00:07
Neighbor Count is 1, Adjacent neighbor count is 1
Crypt Sequence Number is 10
Hello received 260 sent 262, DD received 9 sent 7
LS-Req received 2 sent 2, LS-Upd received 31 sent 8
LS-Ack received 0 sent 20, Discarded 1
Spoke2 # get router info routing-table ospf
Routing table for VRF=0
!!! 192.168.0.X are loopback networks
O 192.168.0.1/32 [110/200] via 192.168.10.1, Spoke2-Phase1, 00:29:45
O 192.168.0.3/32 [110/300] via 192.168.10.1, Spoke2-Phase1, 00:28:14
O 192.168.0.4/32 [110/300] via 192.168.10.1, Spoke2-Phase1, 00:28:04
!!! 192.168.X.0/24 are Hub1's and Spoke's LAN networks
O 192.168.1.0/24 [110/101] via 192.168.10.1, Spoke2-Phase1, 00:29:45
O 192.168.3.0/24 [110/201] via 192.168.10.1, Spoke2-Phase1, 00:28:14
O 192.168.4.0/24 [110/201] via 192.168.10.1, Spoke2-Phase1, 00:07:24
O 192.168.10.1/32 [110/100] via 192.168.10.1, Spoke2-Phase1, 00:29:45
Remarks
In this Part I, we had a design goal that we will minimize the configuration tasks on a hub-and-spoke topology. We have achieved that by creating a dial-up IPSec tunnel in Hub1. So, now when we add a new spoke in the network, we do not need to configure anything on the Hub1. We just need to configure the new Spoke that is added to the network.
The routing topology is that Spoke to Spoke communication is done through Hub which is normal for hub-and-spoke topology. Isn't it nice if we can create a fully mesh network topology where a spoke can talk with another spoke without going to the hub first. And yes that is perfectly possible in our current setup. We will just add one single configuration command in Hub and every Spoke, then we will get a network which is fully meshed logically by IPSec tunnels and that is fortigate's ADVPN.
In part II - we will just configure that (ADVPN).
References
1. Technical Note: Fortinet Auto Discovery VPN (ADVPN)



Thank you for explaining the concepts with example lab.
ReplyDeleteWould you mind sharing the Router configuration with us as well.
If you are looking for router1 configuration, there is nothing in it special. It has 4 interface configured with /30 mask. And fortigates are using it as default gateway so that it can run ipsec towards the hub. In router it is just four /30 connected routes, nothing else.
DeleteThat's what I have configured but the verification is not giving any result for ospf.
DeleteI will reconfigure it and let you know.
First verify local connectivity -
DeleteFor example - ping from spoke2 to hub1 over that 172.16.0.6 to 172.16.0.2.
Do not forget to configure a default route to router1 in fortigate.
Then your tunnel addressing in fortigate must be like this -
edit "Hub1-Phase1"
set ip 192.168.10.1 255.255.255.255
set remote-ip 192.168.10.254 255.255.255.0
Remote IP mask must be /24, otherwise OSPF will not work.
And also careful fortigate is firewall, so necessary firewall rules must be in place. For testing I recommend just disable firewall with an any any allow rule.