IPSec Site-To-Site VPN between Fortigate and Cisco Router
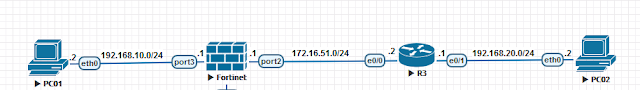
Today I will talk about how to setup a IPSec Site-to-site between a Fortigate firewall and Cisco IOS router. Our network topology looks like this -
All the devices are configured with necessary IP addresses according to the network diagram. Traffic between 192.168.10.0/24 and 192.168.20.0/24 will travel via IPSec tunnel. The tunnel is created over the 172.16.51.0/24 network. In this example the tunnel endpoints are in the same network. In real life they are almost always in different networks controlled by different companies.
We will start configuring the Cisco IOS router first.
Creating isakmp policy (phase 1)
crypto isakmp policy 10
hash md5
encryption des
authentication pre-share
group 5
Here we are defining our policy for phase 1 which are -
In the above figure, we have defined 172.16.51.2 (Cisco router) as our remote peer which is reachable via interface port2.
Now we define our pre-shared key, ike version etc. in the above picture.
We define our encryption and authentication algorithms for phase 1 according to the picture above.
Creating firewall policy
Let's look at the important output from the debug in fortigate, the important information is marked in red -
018-04-18 10:17:54.973854 ike 0:ipsec-direct:1: received p2 notify type RESPONDER-LIFETIME
2018-04-18 10:17:54.975167 ike 0:ipsec-direct:1:ipsec-direct:29: responder selectors 0:192.168.10.0/255.255.255.0:0->0:192.168.20.0/255.255.255.0:0
2018-04-18 10:17:54.977240 ike 0:ipsec-direct:1:ipsec-direct:29: my proposal:
2018-04-18 10:17:54.978379 ike 0:ipsec-direct:1:ipsec-direct:29: proposal id = 1:
2018-04-18 10:17:54.979556 ike 0:ipsec-direct:1:ipsec-direct:29: protocol id = IPSEC_ESP:
2018-04-18 10:17:54.980808 ike 0:ipsec-direct:1:ipsec-direct:29: PFS DH group = 14
2018-04-18 10:17:54.982030 ike 0:ipsec-direct:1:ipsec-direct:29: trans_id = ESP_DES
2018-04-18 10:17:54.983246 ike 0:ipsec-direct:1:ipsec-direct:29: encapsulation = ENCAPSULATION_MODE_TUNNEL
2018-04-18 10:17:54.984815 ike 0:ipsec-direct:1:ipsec-direct:29: type = AUTH_ALG, val=MD5
2018-04-18 10:17:54.985986 ike 0:ipsec-direct:1:ipsec-direct:29: incoming proposal:
2018-04-18 10:17:54.987074 ike 0:ipsec-direct:1:ipsec-direct:29: proposal id = 1:
2018-04-18 10:17:54.988072 ike 0:ipsec-direct:1:ipsec-direct:29: protocol id = IPSEC_ESP:
2018-04-18 10:17:54.989341 ike 0:ipsec-direct:1:ipsec-direct:29: PFS DH group = 14
2018-04-18 10:17:54.990478 ike 0:ipsec-direct:1:ipsec-direct:29: trans_id = ESP_DES
2018-04-18 10:17:54.991639 ike 0:ipsec-direct:1:ipsec-direct:29: encapsulation = ENCAPSULATION_MODE_TUNNEL
2018-04-18 10:17:54.993152 ike 0:ipsec-direct:1:ipsec-direct:29: type = AUTH_ALG, val=MD5
Now we are at the end of the article. I hope it will help somebody who tries to make a manual IPSec tunnel from a fortigate firewall. Most of the examples I found was running a wizard from fortigate which does not breaks up the things like making necessary policies, creating static routes etc.
Further reading and reference -
 |
| IPSec Site-to-Site VPN |
All the devices are configured with necessary IP addresses according to the network diagram. Traffic between 192.168.10.0/24 and 192.168.20.0/24 will travel via IPSec tunnel. The tunnel is created over the 172.16.51.0/24 network. In this example the tunnel endpoints are in the same network. In real life they are almost always in different networks controlled by different companies.
We will start configuring the Cisco IOS router first.
Creating isakmp policy (phase 1)
crypto isakmp policy 10
hash md5
encryption des
authentication pre-share
group 5
Here we are defining our policy for phase 1 which are -
- Encryption - DES
- Authentication - MD5
- D-H group - DH5
- Authentication Method - pre-shared key
Defining pre-shared key and peer
crypto isakmp key juniper address 172.16.51.1
The pre-shared key for the phase 1 and peer ip address is defined by the above command.
Creating IPSec policy (phase 2)
crypto ipsec transform-set myset esp-des esp-md5-hmac
mode tunnel
In phase 2, we are using
- Encryption - DES
- Authentication - MD5
Connecting phase 1 & 2
We have created a access list defining the networks which are reachable over the IPSec tunnel. Here 192.168.20.0/24 is the local network and 192.168.10.0/24 is the remote network. When traffic flows between 192.168.20/24 and 192.168.10.0/24 networks, it will travel through the tunnel.
access-list 100 permit ip 192.168.20.0 0.0.0.255 192.168.10.0 0.0.0.255
Now we will connecting phase 1 and 2 by using a crypto map. Cryptomap is the secret sauce which glues everything together.
crypto map mymap 10 ipsec-isakmp
set peer 172.16.51.1
set transform-set myset
set pfs group5
match address 100
Applying cryptomap to interface
The last stage is to apply the cryptomap to the outgoing interface over which the tunnel will be brought up.
interface Ethernet0/0
crypto map mymap
In our case, it is eth0/0 in Cisco router. It means that when traffic from 192.168.20.0/24 to 192.168.10.0/24 will travel over eth0/0, the IPsec tunnel will be brought up by the router.
Creating necessary route
We also need to create the necessary static route to reach the remote network.
ip route 192.168.10.0 255.255.255.0 Ethernet0/0 172.16.51.1
Because of the cryptomap applied in the previous step, when the traffic is routed towards eth0/0 interface, the interface will start the procedure to bring up the tunnel.
Now we will start configuring the Fortigate firewall. We have created a custom tunnel. In this case defining tunnels, necessary firewall policies and network routes - everything needs to be defined manually.
Configuring phase 1 & 2 in Fortigate
 |
| Defining remote peer |
In the above figure, we have defined 172.16.51.2 (Cisco router) as our remote peer which is reachable via interface port2.
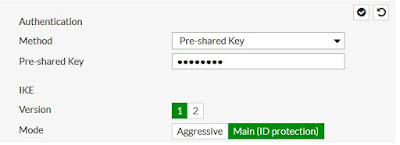 |
| Defining pre-shared key |
Now we define our pre-shared key, ike version etc. in the above picture.
 |
| Defining phase 1 encryption and authentication |
We define our encryption and authentication algorithms for phase 1 according to the picture above.
 |
| IPSec (Phase 2) selectors |
All the necessary information for phase 2 - local/remote networks, encryption, authentication, PFS group etc. is selected in the above picture.
Now we are done with defining out IPSec tunnel.
Creating firewall policy
 |
| Firewall policy |
We have defined two policy. One is for incoming traffic and other is for outgoing traffic. In port3 our local network (192.168.10.0/24) is connected. So, traffic coming from source interface port3, source network 192.168.10.0/24 will be allowed to destination interface ipsec-direct (IPSec interface), destination network 192.168.20.0/24. The other policy is just opposite in direction to allow incoming traffic.
Creating route
 |
| Static route for tunnel |
We have defined a static route which means that traffic to 192.168.20.0/24 will be routed over via ipsec-direct (our tunnel interface) interface.
Verification and troubleshooting
We will try to ping PC01(192.168.10.2) from PC02 (192.168.20.2). A successful ping means the traffic is flowing over the IPSec tunnel.
PC02> ping 192.168.10.2
84 bytes from 192.168.10.2 icmp_seq=1 ttl=62 time=2.336 ms
84 bytes from 192.168.10.2 icmp_seq=2 ttl=62 time=1.667 ms
84 bytes from 192.168.10.2 icmp_seq=3 ttl=62 time=1.571 ms
84 bytes from 192.168.10.2 icmp_seq=4 ttl=62 time=1.455 ms
Let's check the status of our tunnel (phase 1) in Cisco router
Router#show crypto isakmp sa detail
Codes: C - IKE configuration mode, D - Dead Peer Detection
K - Keepalives, N - NAT-traversal
T - cTCP encapsulation, X - IKE Extended Authentication
psk - Preshared key, rsig - RSA signature
renc - RSA encryption
IPv4 Crypto ISAKMP SA
C-id Local Remote I-VRF Status Encr Hash Auth DH Lifetime Cap.
1002 172.16.51.2 172.16.51.1 ACTIVE des md5 psk 5 23:18:27
Engine-id:Conn-id = SW:2
From above we can see that remote peer is 172.16.51.1, status is active. We are using psk (pre-shared key), des, md5 and dh5 as we have configured above.
Let's check the status of our tunnel (phase 2) in Cisco router
Router#show crypto ipsec sa
interface: Ethernet0/0
Crypto map tag: mymap, local addr 172.16.51.2
protected vrf: (none)
local ident (addr/mask/prot/port): (192.168.20.0/255.255.255.0/0/0)
remote ident (addr/mask/prot/port): (192.168.10.0/255.255.255.0/0/0)
current_peer 172.16.51.1 port 500
PERMIT, flags={origin_is_acl,}
#pkts encaps: 5, #pkts encrypt: 5, #pkts digest: 5
#pkts decaps: 5, #pkts decrypt: 5, #pkts verify: 5
#pkts compressed: 0, #pkts decompressed: 0
#pkts not compressed: 0, #pkts compr. failed: 0
#pkts not decompressed: 0, #pkts decompress failed: 0
#send errors 0, #recv errors 0
local crypto endpt.: 172.16.51.2, remote crypto endpt.: 172.16.51.1
plaintext mtu 1446, path mtu 1500, ip mtu 1500, ip mtu idb Ethernet0/0
current outbound spi: 0xBB607876(3143661686)
PFS (Y/N): Y, DH group: group14
inbound esp sas:
spi: 0xAE767792(2926999442)
transform: esp-des esp-md5-hmac ,
in use settings ={Tunnel, }
conn id: 3, flow_id: SW:3, sibling_flags 80000040, crypto map: mymap
sa timing: remaining key lifetime (k/sec): (4264235/928)
IV size: 8 bytes
replay detection support: Y
Status: ACTIVE(ACTIVE)
We can see all the relevant information like local/remote peer, local/remote network, esp settings and number of encrypted packets etc.
If we try the same thing from the fortigate firewall, here "ipsec-direct" is the name of our tunnel.
Below is the information about, phase 1 -
FortiGate # get vpn ike gateway ipsec-direct
vd: root/0
name: ipsec-direct
version: 1
interface: port2 4
addr: 172.16.51.1:500 -> 172.16.51.2:500
created: 408s ago
IKE SA created: 1/1 established: 1/1 time: 3520/3520/3520 ms
IPsec SA created: 1/1 established: 1/1 time: 30/30/30 ms
id/spi: 0 b255068bf7df608e/a77523290d197542
direction: initiator
status: established 408-405s ago = 3520ms
proposal: des-md5
key: de4c7b53c6f96992
lifetime/rekey: 86400/85694
DPD sent/recv: 00000000/00000000
Then information about phase 2 -
FortiGate # get vpn ipsec tunnel name ipsec-direct
gateway
name: 'ipsec-direct'
type: route-based
local-gateway: 172.16.51.1:0 (static)
remote-gateway: 172.16.51.2:0 (static)
mode: ike-v1
interface: 'port2' (4)
rx packets: 14 bytes: 1904 errors: 0
tx packets: 14 bytes: 1176 errors: 1
dpd: on-demand/negotiated idle: 20000ms retry: 3 count: 0
selectors
name: 'ipsec-direct'
auto-negotiate: disable
mode: tunnel
src: 0:192.168.10.0/255.255.255.0:0
dst: 0:192.168.20.0/255.255.255.0:0
SA
lifetime/rekey: 3600/2847
mtu: 1446
tx-esp-seq: f
replay: enabled
inbound
spi: f31b1e15
enc: des 95d335644f2eb107
auth: md5 f15a30188cc7ed844d4896778aada8a4
outbound
spi: 90600d6c
enc: des 2633cbefd25fd37b
auth: md5 1ea8cf3bb0a6b7c65ea76d10bb2b7306
Let's do some debugging now -
In Cisco router, we want to debug the phase 1 (isakmp). We will apply some filter first which defines which tunnel we want to debug.
Router#debug crypto condition peer ipv4 172.16.50.1
Router#debug crypto isakmp
The first command filters out that we want to debug only the tunnel established with peer 172.16.50.1 (fortigate). Then we turn on the debugging with the second command. Following is the debug output when phase 1 is up (important information is marked in red) -
Router#
*Apr 19 14:13:45.091: ISAKMP (1002): received packet from 172.16.51.1 dport 500 sport 500 Global (R) QM_IDLE
*Apr 19 14:13:45.091: ISAKMP: set new node 301106298 to QM_IDLE
*Apr 19 14:13:45.091: ISAKMP:(1002): processing HASH payload. message ID = 301106298
*Apr 19 14:13:45.091: ISAKMP:(1002): processing SA payload. message ID = 301106298
*Apr 19 14:13:45.091: ISAKMP:(1002):Checking IPSec proposal 1
*Apr 19 14:13:45.091: ISAKMP: transform 1, ESP_DES
*Apr 19 14:13:45.091: ISAKMP: attributes in transform:
*Apr 19 14:13:45.091: ISAKMP: SA life type in seconds
*Apr 19 14:13:45.091: ISAKMP: SA life duration (basic) of 43200
*Apr 19 14:13:45.091: ISAKMP: encaps is 1 (Tunnel)
*Apr 19 14:13:45.091: ISAKMP: authenticator is HMAC-MD5
*Apr 19 14:13:45.091: ISAKMP: group is 14
*Apr 19 14:13:45.091: ISAKMP:(1002):atts are acceptable.
*Apr 19 14:13:45.091: ISAKMP:(1002): processing NONCE payload. message ID = 301106298
*Apr 19 14:13:45.091: ISAKMP:(1002): processing KE payload. message ID = 301106298
*Apr 19 14:13:45.103: ISAKMP:(1002): processing ID payload. message ID = 301106298
*Apr 19 14:13:45.103: ISAKMP:(1002): processing ID payload. message ID = 301106298
*Apr 19 14:13:45.103: ISAKMP:(1002):QM Responder gets spi
*Apr 19 14:13:45.103: ISAKMP:(1002):Node 301106298, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Apr 19 14:13:45.103: ISAKMP:(1002):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
*Apr 19 14:13:45.103: ISAKMP:(1002):Node 301106298, Input = IKE_MESG_INTERNAL, IKE_GOT_SPI
*Apr 19 14:13:45.103: ISAKMP:(1002):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_IPSEC_INSTALL_AWAIT
*Apr 19 14:13:45.104: ISAKMP:(1002):Received IPSec Install callback... proceeding with the negotiation
*Apr 19 14:13:45.104: ISAKMP:(1002):Successfully installed IPSEC SA (SPI:0x102069EA) on Ethernet0/0
*Apr 19 14:13:45.104: ISAKMP:(1002): sending packet to 172.16.51.1 my_port 500 peer_port 500 (R) QM_IDLE
Now lets's debug in fortigate. Here we will also filter only the tunnel with peer ip 172.16.51.2 (Cisco).
FortiGate # diagnose vpn ike log-filter dst-addr4 172.16.51.2
FortiGate # diagnose debug application ike -1
FortiGate # diagnose debug enable
If we try the same thing from the fortigate firewall, here "ipsec-direct" is the name of our tunnel.
Below is the information about, phase 1 -
FortiGate # get vpn ike gateway ipsec-direct
vd: root/0
name: ipsec-direct
version: 1
interface: port2 4
addr: 172.16.51.1:500 -> 172.16.51.2:500
created: 408s ago
IKE SA created: 1/1 established: 1/1 time: 3520/3520/3520 ms
IPsec SA created: 1/1 established: 1/1 time: 30/30/30 ms
id/spi: 0 b255068bf7df608e/a77523290d197542
direction: initiator
status: established 408-405s ago = 3520ms
proposal: des-md5
key: de4c7b53c6f96992
lifetime/rekey: 86400/85694
DPD sent/recv: 00000000/00000000
Then information about phase 2 -
FortiGate # get vpn ipsec tunnel name ipsec-direct
gateway
name: 'ipsec-direct'
type: route-based
local-gateway: 172.16.51.1:0 (static)
remote-gateway: 172.16.51.2:0 (static)
mode: ike-v1
interface: 'port2' (4)
rx packets: 14 bytes: 1904 errors: 0
tx packets: 14 bytes: 1176 errors: 1
dpd: on-demand/negotiated idle: 20000ms retry: 3 count: 0
selectors
name: 'ipsec-direct'
auto-negotiate: disable
mode: tunnel
src: 0:192.168.10.0/255.255.255.0:0
dst: 0:192.168.20.0/255.255.255.0:0
SA
lifetime/rekey: 3600/2847
mtu: 1446
tx-esp-seq: f
replay: enabled
inbound
spi: f31b1e15
enc: des 95d335644f2eb107
auth: md5 f15a30188cc7ed844d4896778aada8a4
outbound
spi: 90600d6c
enc: des 2633cbefd25fd37b
auth: md5 1ea8cf3bb0a6b7c65ea76d10bb2b7306
Let's do some debugging now -
In Cisco router, we want to debug the phase 1 (isakmp). We will apply some filter first which defines which tunnel we want to debug.
Router#debug crypto condition peer ipv4 172.16.50.1
Router#debug crypto isakmp
The first command filters out that we want to debug only the tunnel established with peer 172.16.50.1 (fortigate). Then we turn on the debugging with the second command. Following is the debug output when phase 1 is up (important information is marked in red) -
Router#
*Apr 19 14:13:45.091: ISAKMP (1002): received packet from 172.16.51.1 dport 500 sport 500 Global (R) QM_IDLE
*Apr 19 14:13:45.091: ISAKMP: set new node 301106298 to QM_IDLE
*Apr 19 14:13:45.091: ISAKMP:(1002): processing HASH payload. message ID = 301106298
*Apr 19 14:13:45.091: ISAKMP:(1002): processing SA payload. message ID = 301106298
*Apr 19 14:13:45.091: ISAKMP:(1002):Checking IPSec proposal 1
*Apr 19 14:13:45.091: ISAKMP: transform 1, ESP_DES
*Apr 19 14:13:45.091: ISAKMP: attributes in transform:
*Apr 19 14:13:45.091: ISAKMP: SA life type in seconds
*Apr 19 14:13:45.091: ISAKMP: SA life duration (basic) of 43200
*Apr 19 14:13:45.091: ISAKMP: encaps is 1 (Tunnel)
*Apr 19 14:13:45.091: ISAKMP: authenticator is HMAC-MD5
*Apr 19 14:13:45.091: ISAKMP: group is 14
*Apr 19 14:13:45.091: ISAKMP:(1002):atts are acceptable.
*Apr 19 14:13:45.091: ISAKMP:(1002): processing NONCE payload. message ID = 301106298
*Apr 19 14:13:45.091: ISAKMP:(1002): processing KE payload. message ID = 301106298
*Apr 19 14:13:45.103: ISAKMP:(1002): processing ID payload. message ID = 301106298
*Apr 19 14:13:45.103: ISAKMP:(1002): processing ID payload. message ID = 301106298
*Apr 19 14:13:45.103: ISAKMP:(1002):QM Responder gets spi
*Apr 19 14:13:45.103: ISAKMP:(1002):Node 301106298, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Apr 19 14:13:45.103: ISAKMP:(1002):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
*Apr 19 14:13:45.103: ISAKMP:(1002):Node 301106298, Input = IKE_MESG_INTERNAL, IKE_GOT_SPI
*Apr 19 14:13:45.103: ISAKMP:(1002):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_IPSEC_INSTALL_AWAIT
*Apr 19 14:13:45.104: ISAKMP:(1002):Received IPSec Install callback... proceeding with the negotiation
*Apr 19 14:13:45.104: ISAKMP:(1002):Successfully installed IPSEC SA (SPI:0x102069EA) on Ethernet0/0
*Apr 19 14:13:45.104: ISAKMP:(1002): sending packet to 172.16.51.1 my_port 500 peer_port 500 (R) QM_IDLE
Now lets's debug in fortigate. Here we will also filter only the tunnel with peer ip 172.16.51.2 (Cisco).
FortiGate # diagnose vpn ike log-filter dst-addr4 172.16.51.2
FortiGate # diagnose debug application ike -1
FortiGate # diagnose debug enable
Let's look at the important output from the debug in fortigate, the important information is marked in red -
018-04-18 10:17:54.973854 ike 0:ipsec-direct:1: received p2 notify type RESPONDER-LIFETIME
2018-04-18 10:17:54.975167 ike 0:ipsec-direct:1:ipsec-direct:29: responder selectors 0:192.168.10.0/255.255.255.0:0->0:192.168.20.0/255.255.255.0:0
2018-04-18 10:17:54.977240 ike 0:ipsec-direct:1:ipsec-direct:29: my proposal:
2018-04-18 10:17:54.978379 ike 0:ipsec-direct:1:ipsec-direct:29: proposal id = 1:
2018-04-18 10:17:54.979556 ike 0:ipsec-direct:1:ipsec-direct:29: protocol id = IPSEC_ESP:
2018-04-18 10:17:54.980808 ike 0:ipsec-direct:1:ipsec-direct:29: PFS DH group = 14
2018-04-18 10:17:54.982030 ike 0:ipsec-direct:1:ipsec-direct:29: trans_id = ESP_DES
2018-04-18 10:17:54.983246 ike 0:ipsec-direct:1:ipsec-direct:29: encapsulation = ENCAPSULATION_MODE_TUNNEL
2018-04-18 10:17:54.984815 ike 0:ipsec-direct:1:ipsec-direct:29: type = AUTH_ALG, val=MD5
2018-04-18 10:17:54.985986 ike 0:ipsec-direct:1:ipsec-direct:29: incoming proposal:
2018-04-18 10:17:54.987074 ike 0:ipsec-direct:1:ipsec-direct:29: proposal id = 1:
2018-04-18 10:17:54.988072 ike 0:ipsec-direct:1:ipsec-direct:29: protocol id = IPSEC_ESP:
2018-04-18 10:17:54.989341 ike 0:ipsec-direct:1:ipsec-direct:29: PFS DH group = 14
2018-04-18 10:17:54.990478 ike 0:ipsec-direct:1:ipsec-direct:29: trans_id = ESP_DES
2018-04-18 10:17:54.991639 ike 0:ipsec-direct:1:ipsec-direct:29: encapsulation = ENCAPSULATION_MODE_TUNNEL
2018-04-18 10:17:54.993152 ike 0:ipsec-direct:1:ipsec-direct:29: type = AUTH_ALG, val=MD5
Now we are at the end of the article. I hope it will help somebody who tries to make a manual IPSec tunnel from a fortigate firewall. Most of the examples I found was running a wizard from fortigate which does not breaks up the things like making necessary policies, creating static routes etc.
Further reading and reference -



Comments
Post a Comment